What do you learn in cyber security – In the ever-evolving digital landscape, cybersecurity has become an indispensable skill, safeguarding our online presence and protecting sensitive information. Embark on a journey to uncover the intricacies of cybersecurity, empowering yourself with the knowledge to navigate the digital realm with confidence.
From understanding foundational concepts like information and network security to exploring emerging trends such as artificial intelligence and blockchain, this comprehensive guide delves into the multifaceted world of cybersecurity.
Introduction
In the contemporary digital landscape, cybersecurity has emerged as an indispensable safeguard against the myriad threats that lurk within the vast expanse of cyberspace. It encompasses a comprehensive array of measures and practices designed to protect computer systems, networks, and data from unauthorized access, exploitation, or disruption.
The rapid proliferation of internet-connected devices, coupled with the increasing sophistication of cybercriminals, has rendered cybersecurity paramount for both individuals and organizations alike. Its multifaceted nature encompasses a wide range of disciplines, including network security, information security, cloud security, and mobile security, among others.
Foundational Concepts

Cybersecurity encompasses various aspects of protecting information, networks, and cloud systems from unauthorized access, use, disclosure, disruption, modification, or destruction. Foundational concepts in cybersecurity include:
Information Security, What do you learn in cyber security
Information security ensures the confidentiality, integrity, and availability of information. Confidentiality protects information from unauthorized disclosure, while integrity safeguards its accuracy and completeness. Availability ensures that authorized users can access information when needed.
In cyber security, you’ll learn about protecting computer systems and networks from cyberattacks. This includes learning about different types of cyber threats, how to identify and mitigate them, and how to recover from a cyberattack. If you’re interested in learning a new language, you might be wondering how long it takes to learn Russian.
Here’s a helpful guide that can give you an idea of how long it might take, based on your individual learning style and goals. Back to cyber security, you’ll also learn about the legal and ethical implications of cyber security, and how to stay up-to-date on the latest cyber security trends.
Network Security
Network security protects computer networks from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves securing network devices, such as routers, switches, and firewalls, as well as implementing network security protocols and procedures.
Cloud Security
Cloud security protects cloud computing environments, including infrastructure, platforms, and applications. It involves implementing security measures to protect data, access, and resources in the cloud, as well as ensuring compliance with relevant regulations and standards.
Cybersecurity Threats and Vulnerabilities

Cybersecurity threats and vulnerabilities are fundamental concepts in cybersecurity, as they represent the risks that organizations and individuals face in the digital realm. Understanding these threats and vulnerabilities is crucial for implementing effective cybersecurity measures.
Cybersecurity Threats
Cybersecurity threats refer to malicious actions or events that can compromise the security of computer systems, networks, and data. These threats can originate from various sources, including individuals, organized crime groups, and nation-states. Common types of cybersecurity threats include:
- Malware:Malicious software that can damage or disrupt computer systems, such as viruses, worms, and Trojans.
- Phishing:Scams that attempt to trick individuals into revealing sensitive information, such as passwords or credit card numbers.
- Social engineering:Techniques used to manipulate individuals into performing actions that compromise security, such as clicking on malicious links or sharing sensitive information.
Vulnerabilities
Vulnerabilities are weaknesses in computer systems, networks, or software that can be exploited by attackers to gain unauthorized access or compromise the security of the system. These vulnerabilities can exist in hardware, software, or network configurations. Common types of vulnerabilities include:
- Software vulnerabilities:Flaws in software code that can be exploited to gain unauthorized access or execute malicious code.
- Hardware vulnerabilities:Design or implementation flaws in hardware components that can be exploited to compromise the security of the system.
- Network vulnerabilities:Weaknesses in network configurations or protocols that can be exploited to gain unauthorized access or intercept sensitive information.
Cybersecurity Tools and Techniques

Cybersecurity tools and techniques are essential for protecting computer systems and networks from unauthorized access, damage, or disruption. These tools and techniques can be used to detect and prevent attacks, monitor network activity, and respond to security incidents.
Firewalls
Firewalls are network security devices that monitor and control incoming and outgoing network traffic. They can be used to block unauthorized access to a network, prevent the spread of malware, and protect against denial-of-service attacks. Firewalls can be hardware-based, software-based, or a combination of both.
Intrusion Detection Systems
Intrusion detection systems (IDSs) are security devices that monitor network traffic for suspicious activity. They can be used to detect unauthorized access, malware, and other threats. IDSs can be host-based, network-based, or a combination of both.
Vulnerability Scanners
Vulnerability scanners are security tools that scan computer systems and networks for vulnerabilities. They can be used to identify potential security risks and help organizations prioritize their security efforts. Vulnerability scanners can be commercial or open source, and they can be used to scan a variety of operating systems and applications.
Cybersecurity Best Practices
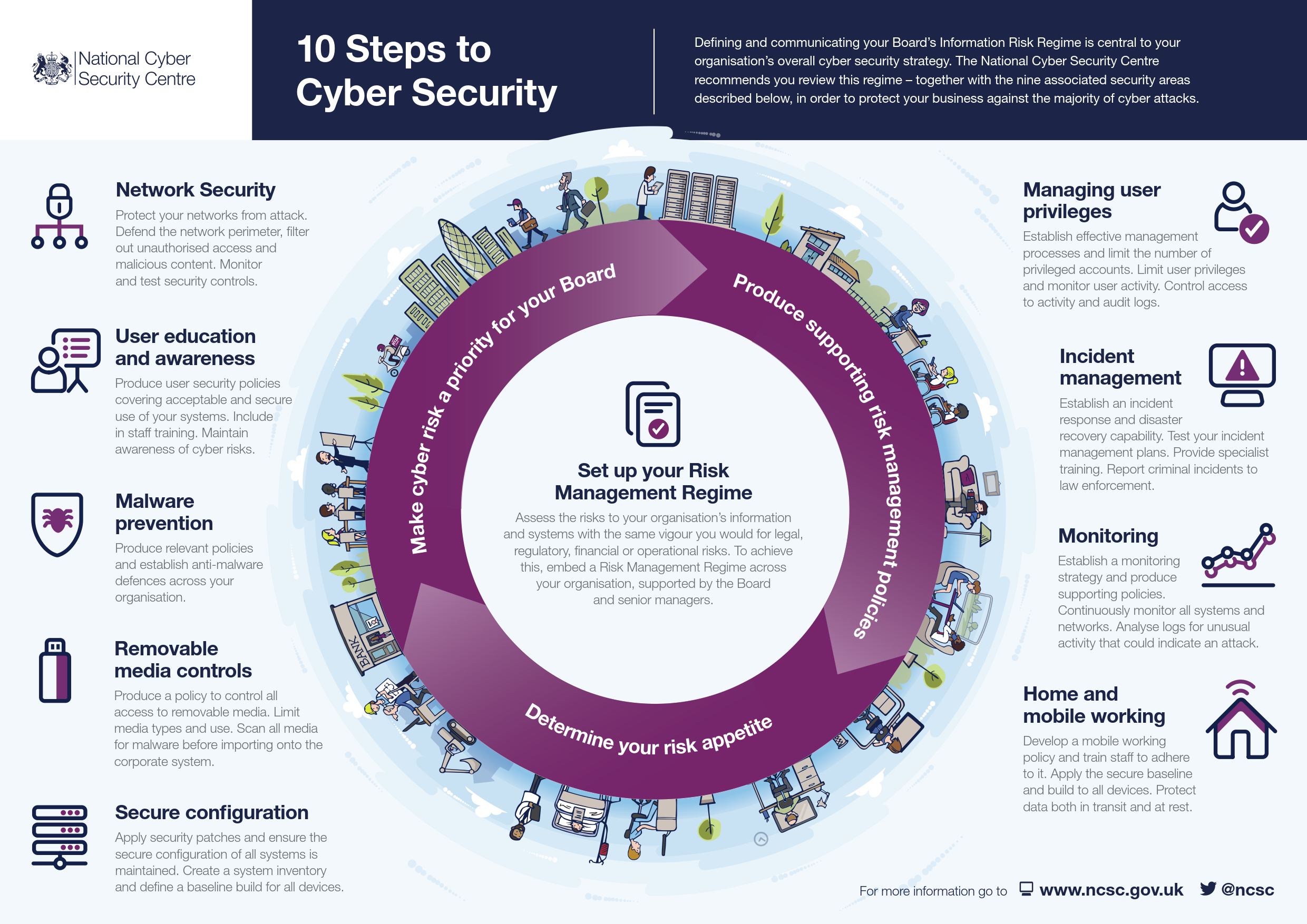
Maintaining cybersecurity requires adherence to best practices that protect against threats and vulnerabilities. These practices encompass password management, data backup, and security awareness training.
Password Management
- Use strong, unique passwords for each account.
- Avoid using personal information or common words in passwords.
- Enable two-factor authentication whenever possible.
- Consider using a password manager to generate and store passwords securely.
Data Backup
Regularly back up important data to prevent loss in case of system failure or cyberattacks.
- Use multiple backup methods, such as external hard drives, cloud storage, or online backup services.
- Keep backups offline or in a secure location to prevent unauthorized access.
- Test backups regularly to ensure they are working properly.
Security Awareness Training
Educate employees and users on cybersecurity threats and best practices to prevent human error and social engineering attacks.
- Provide regular training on topics such as phishing, malware, and social media security.
- Simulate phishing attacks to test employee vigilance.
- Establish clear policies and procedures for handling sensitive information.
Cybersecurity Roles and Responsibilities

Cybersecurity is a multifaceted field that requires a diverse range of expertise. Different roles within the field come with specific responsibilities, ensuring the effective protection of networks and systems.
Security Analysts
Security analysts monitor and analyze security systems, identifying potential threats and vulnerabilities. They are responsible for:
- Reviewing logs and alerts for suspicious activity
- Conducting vulnerability assessments and penetration testing
li>Developing and implementing security policies and procedures
Penetration Testers
Penetration testers simulate cyberattacks to identify vulnerabilities and weaknesses in systems. They work to:
- Identify exploitable vulnerabilities through ethical hacking techniques
- Assess the impact of potential breaches and recommend mitigation strategies
- Provide detailed reports and recommendations to improve security
Incident Responders
Incident responders are responsible for managing and mitigating security incidents. They:
- Respond to security breaches and incidents promptly
- Contain and investigate the extent of the breach
- Implement recovery plans to restore affected systems and data
Emerging Trends in Cybersecurity
Cybersecurity is constantly evolving, with new threats and vulnerabilities emerging all the time. To stay ahead of the curve, it’s important to be aware of the latest trends in cybersecurity.Some of the most important emerging trends in cybersecurity include:
Artificial Intelligence
Artificial intelligence (AI) is a powerful tool that can be used to improve cybersecurity in a number of ways. For example, AI can be used to:
- Detect and respond to threats more quickly and effectively
- Identify and mitigate vulnerabilities
- Develop new security solutions
Machine Learning
Machine learning (ML) is a subset of AI that allows computers to learn from data without being explicitly programmed. ML can be used to improve cybersecurity in a number of ways, including:
- Detecting and classifying threats
- Identifying anomalies in data
- Predicting future attacks
Blockchain
Blockchain is a distributed ledger technology that is used to create secure, transparent, and tamper-proof records. Blockchain can be used to improve cybersecurity in a number of ways, including:
- Storing and managing security logs
- Creating secure identities
- Developing new security solutions
Cybersecurity Education and Training

Cybersecurity education and training are crucial to protect individuals, organizations, and nations from cyber threats. It equips individuals with the knowledge, skills, and abilities to identify, prevent, detect, and respond to cyberattacks.
In cybersecurity, you’ll master skills like protecting networks, defending against cyber threats, and investigating digital crimes. If you’re looking to expand your skillset in a different direction, check out this guide on how to learn a new talent in potion craft . Back in cybersecurity, you’ll also learn about ethical hacking, incident response, and risk management.
Types of Cybersecurity Certifications and Training Programs
There are numerous cybersecurity certifications and training programs available, ranging from entry-level to advanced levels. Some popular certifications include:
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- CompTIA Security+
- Certified Information Security Manager (CISM)
- Offensive Security Certified Professional (OSCP)
Cybersecurity Career Paths

The cybersecurity landscape offers a wide range of career paths, each requiring specialized skills and knowledge. From protecting networks to conducting security audits, there’s a role for every aptitude and interest.
The job outlook for cybersecurity professionals is exceptionally promising, with an increasing demand for skilled individuals driven by the growing prevalence of cyber threats and data breaches. The earning potential is equally attractive, with cybersecurity professionals earning competitive salaries and benefits packages.
Cybersecurity Analyst
Cybersecurity analysts are responsible for monitoring, detecting, and responding to cyber threats. They analyze security data, investigate incidents, and develop security strategies to protect organizations from cyberattacks.
Penetration Tester
Penetration testers, also known as ethical hackers, simulate cyberattacks to identify vulnerabilities in an organization’s systems. They provide recommendations for strengthening security measures and improving the overall security posture.
Security Architect
Security architects design, implement, and maintain the security infrastructure of an organization. They collaborate with stakeholders to assess security risks, develop security policies, and implement technical solutions to protect sensitive data and systems.
Cybersecurity Manager
Cybersecurity managers oversee the cybersecurity program of an organization. They lead a team of cybersecurity professionals, manage security budgets, and ensure compliance with industry regulations.
Incident Responder
Incident responders are responsible for responding to and managing security incidents. They investigate the incident, contain the damage, and restore normal operations as quickly as possible.
FAQ Corner: What Do You Learn In Cyber Security
What are the most common cybersecurity threats?
Malware, phishing, social engineering, ransomware, and DDoS attacks are among the most prevalent cybersecurity threats.
How can I protect my personal information online?
Use strong passwords, enable two-factor authentication, be cautious of suspicious emails and websites, and keep your software up to date.
What are the benefits of cybersecurity training?
Cybersecurity training enhances your understanding of cyber threats, improves your ability to protect your systems, and prepares you for a rewarding career in the field.